Originally published in Defense Acquisition Magazine, January-February 2024. Cory Yoder is a senior lecturer of Acquisition Management in the Department of Defense Management.
Hostile forces can hide among commercial suppliers for DoD’s overseas operations and surface suddenly to harm U.S. interests at critical moments. DoD is developing needed protocols and processes to identify “bad actors” and prevent them from receiving contract awards or gaining access to military operations and installations abroad. Additional legislation, DoD directives and instructions, and DAU and other training will provide greater security against such risks. Still more needs to be done in a time of rising global tensions with both state and nonstate actors.
The department must rely on many commercial sources for services and supplies as it projects and sustains military power globally in both steady-state and contingency operations. Commercial sources with contrary objectives and interests can create immediate risks to U.S. forces, operational objectives, and long-term national security outcomes.
The joint force relies on commercial capability and capacity for many services, including logistics, communications, construction, and language translation. In recent operations, commercial support has comprised a significant percentage of the total deployed force. As a result, DoD needs to be fully on guard against its potential risks.
Vendor Threat Mitigation (VTM) is the DoD program to identify threats and manage the associated risk posed by vendors supporting operations outside the United States. VTM leverages all-source information and Combatant Commander guidance to identify vendors that support U.S. adversaries.
Broadly, the VTM program supports delivery of sustainable logistics to support DoD mission requirements by establishing and improving vendor vetting policy, processes, and procedures to enhance and protect mission operations.
While programs like Supply Chain Risk Management cover large-scale technology and cyber purchases from major U.S. and partner country suppliers, VTM is needed to address services and basic commodities obtained from smaller foreign-owned vendors, such as fuel or base perimeter construction and materials.
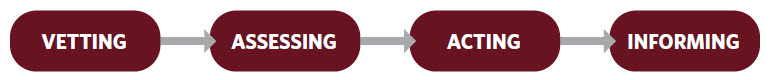
The VTM process (Figure 1) is a programmatic approach that includes the following:
Vetting. Leveraging all-source information to identify threats posed by vendors that support U.S. adversaries.
Assessing. Considering the potential risks to combatant command objectives and U.S. missions and forces.
Acting. Coordinating appropriate risk management actions with supported units and contracting activities.
Informing. Sharing information within the DoD and across the Whole of Government.
Figure 1. VTM Process
Vendor risks may include but are not limited to using U.S. funding to support U.S. adversaries; communicating critical intelligence to adversaries; exploiting U.S. technology against U.S. capabilities; providing compromised services and goods to U.S. forces; and acquiring physical or virtual access to U.S. enclaves to enable harmful acts.
How Does VTM Work?
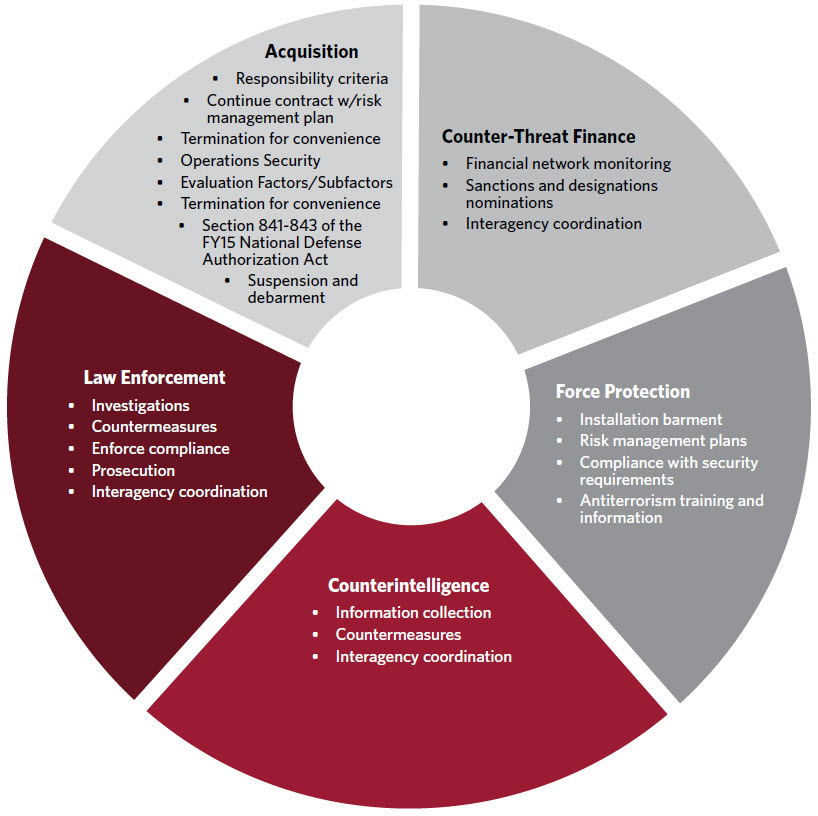
VTM programs have a range of options and authorities to manage threat-based risk of commercial support, including force protection, acquisition remedies, counter-threat finance, counterintelligence, and legal provisions. VTM programs will not use each of these options in equal degree or frequency. The best option(s) will be case-specific and depend on mission requirements, criticality of the capability, command priorities, available resources, and time. A review of the options and authorities is provided in Figure 2.
Origins of VTM
DoD Directive (DoDD) 3000.16, Vendor Threat Mitigation, July 6, 2022, established the present-day VTM program. Prior to this policy, however, congressional action and legislation drove the creation of some VTM capabilities.
In 2008, Congress established the Commission on Wartime Contracting in Iraq and Afghanistan and tasked it with examining a range of issues related to wartime contracting, including the extent of fraud, abuse, and mismanagement of wartime contracts. The Commission identified diversion of U.S. government funds to insurgents in Afghanistan as a major concern. The Commissioners stated that the extortion of funds from U.S. construction projects and transportation contracts was the second-largest funding source for the insurgents.
Congress enacted legislation allowing the DoD to manage the risk of funds flowing to enemies of the United States in designated contingency operations.
Section 841-843 of the National Defense Authorization Act (NDAA) for fiscal year (FY) 2012, titled “Never Contract with the Enemy,” directed the Secretary of Defense to develop a process by which the Combatant Commander of the U.S. Central Command (USCENTCOM) would identify entities with a contract, grant, or cooperative agreement actively supporting an insurgency or actively opposing the United States. Furthermore, the head of a contracting activity was authorized to restrict, terminate, or void contracts that would provide funds directly or indirectly to such persons or entities. Use of the authority was limited to declared contingency operations with active hostilities in USCENTCOM.
The legislation was expanded to apply to additional Combatant Commands in FY14 and FY15, and the sunset was extended through 2025 in the FY23 NDAA. However, the limitations on its use related to operational conditions remain in place. It applies to overseas contingency operations under formal declaration with hostilities. This legislation is one of many tools that Combatant Commanders can apply to address commercial support risks.
Figure 2. VTM Options for Managing Risk
Implementation in Combatant Commands
Combatant Commanders are responsible for planning and executing missions within their functional or geographic areas of responsibility. They anticipate and set conditions for the commands, determine risk, set command relationships, and prioritize effort and support. Combatant Commanders are supported by subordinate commanders, who execute their duties within their own component commands under the conditions set by the Combatant Commander. Each Combatant Command has different mission sets, geographies, or functions and priorities and may approach VTM differently. It is important to determine whether there is Combatant Command-specific guidance for VTM and understand any existing processes. With the various worldwide locations of Combatant Commands, the success of achieving VTM goals may require differing processes and responsibilities to ensure resources are used efficiently for each unique location. However, the basic hallmarks remain the same throughout all locations.
"It is important to determine whether there is Combatant Command-specific guidance for VTM and understand any existing processes."
Best Practices Working Group
VTM is inherently cross-functional, spanning acquisition, intelligence, legal, operations, force protection, and security.
DoD established a VTM working group to coordinate activities and intelligence among the various relevant DoD organizations. The group examines strategic matters related to operational vendor threat issues and supports related policy and process development in coordination with the Whole of Government.
The VTM Working Group also coordinates legislation and carries out policy and regulations, supports capability development, and shares VTM information.
As stated in DoDD 3000.16, Vendor Threat Mitigation, the DoD is responsible for coordinating with other U.S. Government departments and agencies on VTM activities in accordance with applicable laws, regulations, policy, agreements, and arrangements.
The DoD also is responsible for sharing VTM information on threats posed by vendors to include intelligence reports and products, threat assessments, and risk assessments.
The DoD’s VTM partner organizations include the Departments of Commerce, Homeland Security, State, and Treasury as well as the General Services Administration, the Office of the Director of National Intelligence, and the U.S. Agency for International Development.
Training and Education
As Combatant Commands develop and mature their VTM programs, the Services are responsible for ensuring well-trained personnel are available to perform VTM-related tasks. Training standards, tactics, techniques, and procedures will be developed to inform joint force and Service-specific training.
DAU CON 0840 Vendor Threat Mitigation (VTM) is an online training course established in August 2023 that provides students with a broad introduction to the policies and functions for VTM and the importance of considering the potential risks introduced by malign actors in campaign and contingency operations. The course defines VTM, reviews roles and responsibilities for various government stakeholders involved, and provides examples of VTM policies from various Combatant Commands and operations. This course targets DoD acquisition and nonacquisition professionals, especially supply chain security professionals; joint and Service component headquarters staffs with force protection, counterintelligence, and operational contract support responsibilities; and contracting activities supporting overseas campaign and contingency operations.
Ultimately, these efforts will support readiness reporting on VTM and incorporation of VTM-related tasks into exercises and other training events.
Current Trends
Strengthening the DoD’s capability to perform VTM effectively and efficiently is of paramount importance. Policy, directives, and legislative initiatives and recommendations include the following.
Future VTM policy. There has been considerable activity on Vendor Threat Intelligence within the DoD, the intelligence community, and across the government, especially since DoDD 3000.16 was issued in July 2022.
The Office of the Under Secretary of Defense for Acquisition and Sustainment is developing a DoD Instruction (DoDI) on the VTM program to define and standardize procedures and guidelines across the DoD. Additionally, the Office of the Under Secretary of Defense for Intelligence and Security is developing a DoDI that will provide the Defense Intelligence Enterprise with guidance on providing intelligence support to VTM.
More detailed guidance and procedures may be developed once these policy milestones are achieved, which will provide Combatant Commanders and others involved in the VTM process tools and procedures to address risks from contracted support with enough flexibility to deal with the broad and unique array of possible scenarios.
Policy. As stated previously, a DoDI on VTM is under development to define procedures and establish standards. A separate Instruction is under development to provide the Defense Intelligence Enterprise with guidance on intelligence support to VTM.
Legislation. The FY24 National Defense Authorization Act (NDAA)includes a proposal to extend and expand authorities in Sections 841–843 of the FY15 NDAA that prohibit providing funds to the enemy. The DoD seeks new statutory authorities through a legislative proposal to expand Sections 841–843 of the FY15 NDAA to all Combatant Commands, regardless of contingency declaration status. This would allow commanders to work with their contracting counterparts and to mitigate significant risk and terminate, void, or restrict contracts, grants, and cooperative agreements based on the risks identified in intelligence reports. DoD could lawfully access intelligence, financial, law enforcement, and other information on vendors supporting operations to thoroughly assess threats. The authorities could continue indefinitely.
Training. DAU has developed an “Intro to VTM” course offering. In addition, the course developers have taken initial actions to integrate VTM into Universal Joint Tasks.
Oversight. The DoD authorized the VTM Executive Council on April 6, 2023. The Council established the strategic direction for the VTM program and approved recommendations to pursue its objectives.
"Many vendors cannot get through the system qualifiers to receive contracts due to limitations with literacy, language, and computer competence."
Conclusion and Recommendations
The authors offer the following recommendations to strengthen and improve the VTM program and processes:
- First, revise the current legislation and NDAA that restrict VTM to declared overseas contingencies with active hostilities only. Expand VTM to include all operations.
- Second, recommend that the Office of the Secretary of Defense create a VTM guidebook of protocols and best practices for activities interested in pursuing and implementing efficient and effective VTM processes and protocols in their own activities, while simultaneously capitalizing on what is learned by those on the front lines.
- Third, develop robust, yet unobtrusive, data metrics on VTM processing times and decision accuracy.
- Fourth, keep existing process in place where “working groups” provide decision analysis and recommendations for higher authority decision making for vendor exclusion or other actions.
- Fifth, ensure that contracting officer and contracting officer representative vendor assessment information is included in the VTM assessment data and decision process.
- Sixth, include and continue VTM training and education at DAU, Naval Postgraduate School, and Professional Military Education programs designed to train and educate the DoD contracting and acquisition workforce and all commands’ support operations.
- Seventh, include a language translation capability within Joint Contingency Contracting System (JCCS) to facilitate foreign vendor registration in JCCS.
- Eighth, include a computer literacy liaison who can assist vendors with limitations to complete the JCCS registration process. Many vendors cannot get through the system qualifiers to receive contracts due to limitations with literacy, language, and computer competence.
Incorporating these recommendations and expanding Section 841 authorities will greatly enhance VTM program capabilities. An expanded such authority would apply across the DoD. It could and should be expanded to Whole of Government agencies issuing contracts overseas.
VTM is an essential program in today’s great power competition. It plays a key role in ensuring that the threats posed by reliance on commercial sources are minimized, while simultaneously considering the operational balance such support provides to the global supply chain. It is imperative that Combatant Commands embrace current requirements and best practices to create and utilize VTM to help prevent “bad actors” from receiving contract awards. The need for the VTM program will continue to increase as the United States becomes more operationally active in gray zone areas where competitors and adversaries are using DoD’s reliance on commercial support to seek advantage.
VTM’s ultimate goals include seeking authorities to address gaps as they are identified, establish policy and doctrine to institutionalize VTM, and develop and mature DoD-wide VTM training and vigilance.
Read the article as published in Defense Acquisition magazine.

